服务器:windows 2008 r2,tomcat 7
测试页面:jsp
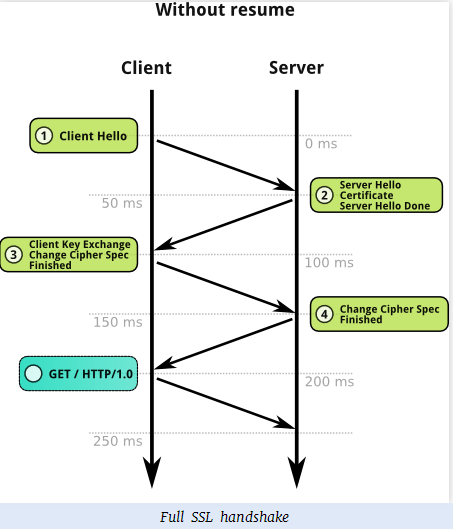
过程:打开wireshark开始抓包,过滤ssl,谷歌浏览器输入https网址,wireshark中能观察到https链接建立的握手过程,浏览器发送client hello 后,在服务器返回的server hello中,如下:
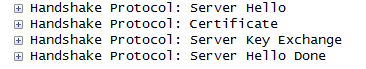
之后刷新网页,服务器返回的server hello,如下:
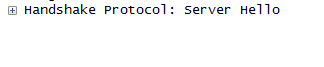
少了发送证书后面的一些信息,其中server hello中的session ID的值相同。
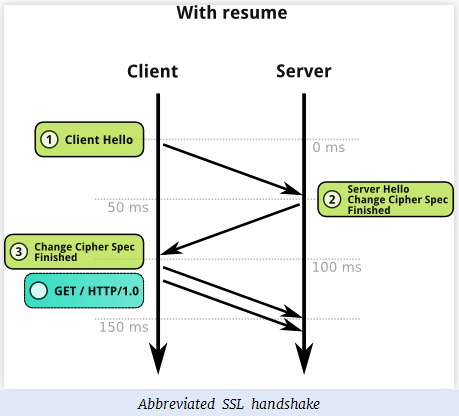
百度了一下,当客户端想要恢复以前的会话时流程如下,不是进行完整的秘钥协商过程的。
Client Server
ClientHello -------->
ServerHello
[ChangeCipherSpec]
<-------- Finished
[ChangeCipherSpec]
Finished -------->
Application Data <-------> Application Data
之后我间隔10分钟、20分钟、30分钟刷新网页,发现30分钟之后,服务器又会发送证书等信息了,此时server hello中的session ID的值与之前不同。
疑问:刷新https网页是否进行完整的秘钥协商过程是由谁决定的(服务器、客户端)?这个时限又是由谁决定的?如何配置?
求大神解惑。
 发帖
发帖 与我相关
与我相关 我的任务
我的任务 分享
分享