576
社区成员
 发帖
发帖 与我相关
与我相关 我的任务
我的任务 分享
分享开发环境:Windows 11
DevEco Studio 版本:DevEco Studio 3.1 Release(3.1.0.500)
SDK 版本:3.2.12.5(Full SDK)
开发板型号:DAYU 200
系统版本:OpenHarmony 3.2 Release
涉及仓库:Hap包签名工具[developtools_hapsigner]
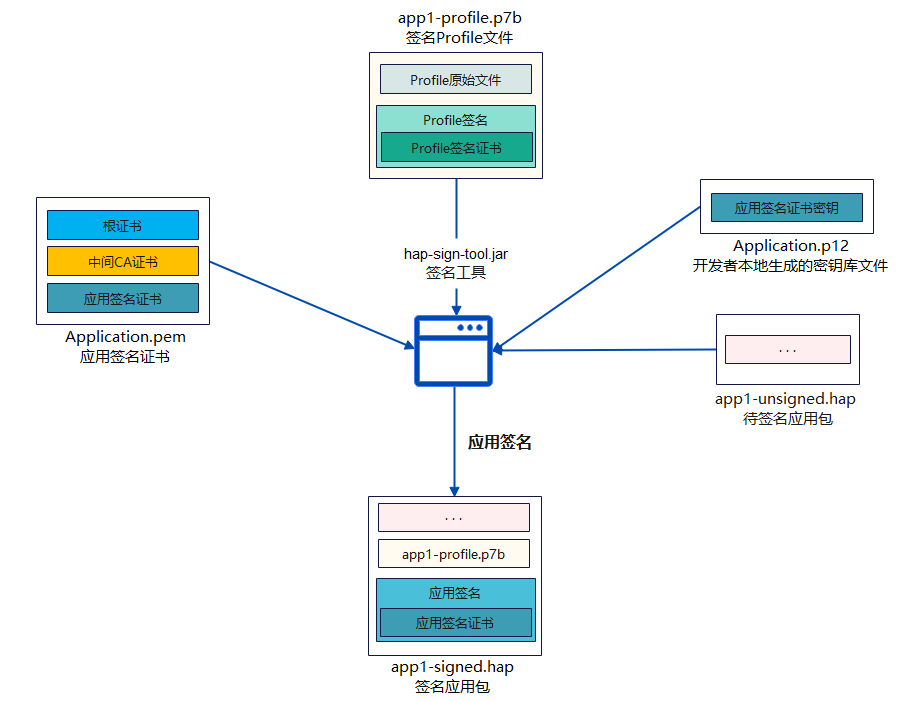
为了保证OpenHarmony应用的完整性和来源可靠,在应用构建时需要对应用进行签名。经过签名的应用才能在真机设备上安装、运行、和调试。developtools_hapsigner仓提供了签名工具的源码,包含密钥对生成、CSR文件生成、证书生成、Profile文件签名、Hap包签名等功能。
OpenHarmony系统中有一套默认签名信息,用于应用的开发和调试。当系统厂商正式发布系统时,需要新增或替换私有签名信息,本篇文档将介绍如何生成私有签名并在系统中进行配置。本文档需准备Java和Gradle编译环境。
Profile签名场景:

应用签名场景:
1. 克隆developtools_hapsigner仓库
git clone https://gitee.com/openharmony/developtools_hapsigner.git
2. 命令行打开文件目录至developtools_hapsigner/hapsigntool,执行命令进行编译打包
gradle build 或者 gradle jar
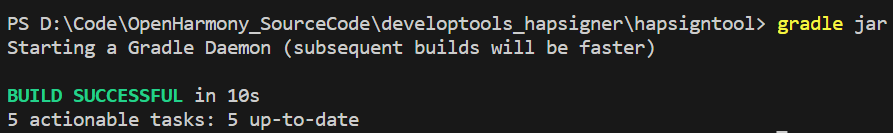
3. 编译后得到二进制文件,目录为:
developtools_hapsigner/hapsigntool/hap_sign_tool/build/libs/hap-sign-tool.jar

generate-keypair :
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -keyAlg # 密钥算法,必填项,包括RSA/ECC
├── -keySize # 密钥长度,必填项,RSA算法的长度为2048/3072/4096,ECC算法的长度NIST-P-256/NIST-P-384
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
generate-csr :
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -subject # 证书主题,必填项
├── -signAlg # 签名算法,必填项,包括SHA256withRSA / SHA384withRSA / SHA256withECDSA / SHA384withECDSA
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出文件,可选项,如果不填,则直接输出到控制台
generate-ca :
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -keyAlg # 密钥算法,必填项,包括RSA/ECC
├── -keySize # 密钥长度,必填项,RSA算法的长度为2048/3072/4096,ECC算法的长度NIST-P-256/NIST-P-384
├── -issuer # 颁发者的主题,可选项,如果不填,表示根CA
├── -issuerKeyAlias # 颁发者的密钥别名,可选项,如果不填,表示根CA
├── -issuerKeyPwd # 颁发者的密钥口令,可选项
├── -subject # 证书主题,必填项
├── -validity # 证书有效期,可选项,默认为3650天
├── -signAlg # 签名算法,必填项,包括SHA256withRSA / SHA384withRSA / SHA256withECDSA / SHA384withECDSA
├── -basicConstraintsPathLen # 路径长度,可选项,默认为0
├── -issuerKeystoreFile # 签发者密钥库文件,可选项,JKS或P12格式
├── -issuerKeystorePwd # 签发者密钥库口令,可选项
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出文件,可选项,如果不填,则直接输出到控制台
generate-app-cert :
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -issuer # 颁发者的主题,必填项
├── -issuerKeyAlias # 颁发者的密钥别名,必填项
├── -issuerKeyPwd # 颁发者的密钥口令,可选项
├── -subject # 证书主题,必填项
├── -validity # 证书有效期,可选项,默认为3650天
├── -signAlg # 签名算法,必填项,包括SHA256withECDSA / SHA384withECDSA;
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -issuerKeystoreFile # 签发者密钥库文件,可选项,JKS或P12格式
├── -issuerKeystorePwd # 签发者密钥库口令,可选项
├── -outForm # 输出证书文件的格式,包括 cert / certChain,可选项,默认为certChain
├── -rootCaCertFile # outForm为certChain时必填,根CA证书文件
├── -subCaCertFile # outForm为certChain时必填,中间CA证书文件
├── -outFile # 输出证书文件(证书或证书链),可选项,如果不填,则直接输出到控制台
generate-profile-cert :
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -issuer # 颁发者的主题,必填项
├── -issuerKeyAlias # 颁发者的密钥别名,必填项
├── -issuerKeyPwd # 颁发者的密钥口令,可选项
├── -subject # 证书主题,必填项
├── -validity # 证书有效期,可选项,默认为3650天
├── -signAlg # 签名算法,必填项,包括SHA256withECDSA / SHA384withECDSA;
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -issuerKeystoreFile # 签发者密钥库文件,可选项,JKS或P12格式
├── -issuerKeystorePwd # 签发者密钥库口令,可选项
├── -outForm # 输出证书文件的格式,包括 cert / certChain,可选项,默认为certChain
├── -rootCaCertFile # outForm为certChain时必填,根CA证书文件
├── -subCaCertFile # outForm为certChain时必填,中间CA证书文件
├── -outFile # 输出证书文件(证书或证书链),可选项,如果不填,则直接输出到控制台
generate-cert :
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -issuer # 颁发者的主题,必填项
├── -issuerKeyAlias # 颁发者的密钥别名,必填项
├── -issuerKeyPwd # 颁发者的密钥口令,可选项
├── -subject # 证书主题,必填项
├── -validity # 证书有效期,可选项,默认为1095天
├── -keyUsage # 密钥用法,必选项,包括digitalSignature, nonRepudiation, keyEncipherment,
├ dataEncipherment, keyAgreement, certificateSignature, crlSignature,
├ encipherOnly和decipherOnly,如果证书包括多个密钥用法,用逗号分隔
├── -keyUsageCritical # keyUsage是否为关键项,可选项,默认为是
├── -extKeyUsage # 扩展密钥用法,可选项,包括clientAuthentication,serverAuthentication,
├ codeSignature,emailProtection,smartCardLogin,timestamp,ocspSignature
├── -extKeyUsageCritical # extKeyUsage是否为关键项,可选项,默认为否
├── -signAlg # 签名算法,必填项,包括SHA256withRSA/SHA384withRSA/SHA256withECDSA/SHA384withECDSA
├── -basicConstraints # 是否包含basicConstraints,可选项,默认为否
├── -basicConstraintsCritical # basicConstraints是否包含为关键项,可选项,默认为否
├── -basicConstraintsCa # 是否为CA,可选项,默认为否
├── -basicConstraintsPathLen # 路径长度,可选项,默认为0
├── -issuerKeystoreFile # 签发者密钥库文件,可选项,JKS或P12格式
├── -issuerKeystorePwd # 签发者密钥库口令,可选项
├── -keystoreFile # 密钥库文件,必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出证书文件,可选项,如果不填,则直接输出到控制台
sign-profile :
├── -mode # 签名模式,必填项,包括localSign,remoteSign
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -profileCertFile # Profile签名证书(证书链,顺序为最终实体证书-中间CA证书-根证书),必填项
├── -inFile # 输入的原始Provision Profile文件,必填项
├── -signAlg # 签名算法,必填项,包括SHA256withECDSA / SHA384withECDSA
├── -keystoreFile # 密钥库文件,localSign模式时为必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出签名后的Provision Profile文件,p7b格式,必填项
verify-profile :
├── -inFile # 已签名的Provision Profile文件,p7b格式,必填项
├── -outFile # 验证结果文件(包含验证结果和profile内容),json格式,可选项;如果不填,则直接输出到控制台
sign-app :
├── -mode # 签名模式,必填项,包括localSign,remoteSign,remoteResign
├── -keyAlias # 密钥别名,必填项
├── -keyPwd # 密钥口令,可选项
├── -appCertFile # 应用签名证书文件(证书链,顺序为最终实体证书-中间CA证书-根证书),必填项
├── -profileFile # 签名后的Provision Profile文件名,profileSigned为1时为p7b格式,profileSigned为0时为json格式,必填项
├── -profileSigned # 指示profile文件是否带有签名,1表示有签名,0表示没有签名,默认为1。可选项
├── -inForm # 输入的原始文件的格式,zip格式或bin格式,默认zip格式,可选项
├── -inFile # 输入的原始APP包文件,zip格式或bin格式,必填项
├── -signAlg # 签名算法,必填项,包括SHA256withECDSA / SHA384withECDSA
├── -keystoreFile # 密钥库文件,localSign模式时为必填项,JKS或P12格式
├── -keystorePwd # 密钥库口令,可选项
├── -outFile # 输出签名后的包文件,必填项
verify-app :
├── -inFile # 已签名的应用包文件,zip格式或bin格式,必填项
├── -outCertChain # 签名的证书链文件,必填项
├── -outProfile # 应用包中的profile文件,必填项
1. 生成密钥对,keystorePwd为密钥库口令。
java -jar hap-sign-tool.jar generate-keypair -keyAlias "OpenHarmony-Tizi" -keyAlg "ECC" -keySize "NIST-P-256" -keystoreFile "OpenHarmony-Tizi.p12" -keyPwd "Pwd-Tizi-1" -keystorePwd "Pwd-Tizi-2"
2. 生成RootCA证书,subject为RootCA的证书主题,用于配置trusted_root_ca.json。
java -jar hap-sign-tool.jar generate-ca -keyAlias "OpenHarmony-Tizi-rootCA" -signAlg "SHA256withECDSA" -keyAlg "ECC" -keySize "NIST-P-256" -subject "C=CN, O=OpenHarmony-Tizi-rootCA, OU=OpenHarmony-Tizi-rootCA Community, CN=OpenHarmony Application Root CA" -keystoreFile "OpenHarmony-Tizi.p12" -outFile "OpenHarmony-Tizi-rootCA.cer" -keyPwd "Pwd-Tizi-3" -keystorePwd "Pwd-Tizi-2" -validity "365"
3. 生成SubCA证书。
java -jar hap-sign-tool.jar generate-ca -keyAlias "OpenHarmony-Tizi-subCA" -signAlg "SHA256withECDSA" -keyAlg "ECC" -keySize "NIST-P-256" -subject "C=CN, O=OpenHarmony-Tizi-subCA, OU=OpenHarmony-Tizi-subCA Community, CN=OpenHarmony Application Sub CA" -keystoreFile "OpenHarmony-Tizi.p12" -outFile "OpenHarmony-Tizi-subCA.cer" -keyPwd "Pwd-Tizi-4" -keystorePwd "Pwd-Tizi-2" -issuer "C=CN, O=OpenHarmony-Tizi-rootCA, OU=OpenHarmony-Tizi-rootCA Community, CN=OpenHarmony Application Root CA" -issuerKeyAlias "OpenHarmony-Tizi-rootCA" -issuerKeyPwd "Pwd-Tizi-3" -validity "365"
4. 生成应用调试/发布证书,subject用于配置trusted_apps_sources.json中的app-signing-cert项。
java -jar hap-sign-tool.jar generate-app-cert -keyAlias "OpenHarmony-Tizi-subCA" -signAlg "SHA256withECDSA" -subject "C=CN, O=OpenHarmony-Tizi-app-cert, OU=OpenHarmony-Tizi-app-cert Community, CN=OpenHarmony Application Release" -keystoreFile "OpenHarmony-Tizi.p12" -subCaCertFile "OpenHarmony-Tizi-subCA.cer" -rootCaCertFile "OpenHarmony-Tizi-rootCA.cer" -outForm "certChain" -outFile "OpenHarmony-Tizi-app-cert.pem" -keyPwd "Pwd-Tizi-4" -keystorePwd "Pwd-Tizi-2" -issuer "C=CN, O=OpenHarmony-Tizi-subCA, OU=OpenHarmony-Tizi-subCA Community, CN=OpenHarmony Application Sub CA" -issuerKeyAlias "OpenHarmony-Tizi-subCA" -issuerKeyPwd "Pwd-Tizi-4" -validity "365"
5. 生成ProfileCA证书,subject用于配置trusted_apps_sources.json中的issuer-ca项。
java -jar hap-sign-tool.jar generate-ca -keyAlias "OpenHarmony-Tizi-profileCA" -signAlg "SHA256withECDSA" -keyAlg "ECC" -keySize "NIST-P-256" -subject "C=CN, O=OpenHarmony-Tizi-subCA, OU=OpenHarmony-Tizi-subCA Community, CN=OpenHarmony Application CA" -keystoreFile "OpenHarmony-Tizi.p12" -outFile "OpenHarmony-Tizi-profileCA.cer" -keyPwd "Pwd-Tizi-5" -keystorePwd "Pwd-Tizi-2" -issuer "C=CN, O=OpenHarmony-Tizi-rootCA, OU=OpenHarmony-Tizi-rootCA Community, CN=OpenHarmony Application Root CA" -issuerKeyAlias "OpenHarmony-Tizi-rootCA" -issuerKeyPwd "Pwd-Tizi-3" -validity "365"
6. 生成应用Release版profile调试/发布证书,subject用于配置trusted_apps_sources.json中的profile-signing-certificate项。
jar hap-sign-tool.jar generate-profile-cert -keyAlias "OpenHarmony-Tizi-profileCA" -signAlg "SHA256withECDSA" -subject "C=CN, O=OpenHarmony-Tizi-profile-cert, OU=OpenHarmony-Tizi-profile-cert Community, CN=OpenHarmony Application Profile Release" -keystoreFile "OpenHarmony-Tizi.p12" -subCaCertFile "OpenHarmony-Tizi-profileCA.cer" -rootCaCertFile "OpenHarmony-Tizi-rootCA.cer" -outForm "certChain" -outFile "OpenHarmony-Tizi-profile-cert-release.pem" -keyPwd "Pwd-Tizi-5" -keystorePwd "Pwd-Tizi-2" -issuer "C=CN, O=OpenHarmony-Tizi-subCA, OU=OpenHarmony-Tizi-subCA Community, CN=OpenHarmony Application CA" -issuerKeyAlias "OpenHarmony-Tizi-profileCA" -issuerKeyPwd "Pwd-Tizi-5" -validity "365"
7. 生成应用Debug版profile调试/发布证书,subject用于配置trusted_apps_sources.json中的profile-debug-signing-certificate项。
java -jar hap-sign-tool.jar generate-profile-cert -keyAlias "OpenHarmony-Tizi-profileCA" -signAlg "SHA256withECDSA" -subject "C=CN, O=OpenHarmony-Tizi-profile-cert, OU=OpenHarmony-Tizi-profile-cert Community, CN=OpenHarmony Application Profile Debug" -keystoreFile "OpenHarmony-Tizi.p12" -subCaCertFile "OpenHarmony-Tizi-profileCA.cer" -rootCaCertFile "OpenHarmony-Tizi-rootCA.cer" -outForm "certChain" -outFile "OpenHarmony-Tizi-profile-cert-debug.pem" -keyPwd "Pwd-Tizi-5" -keystorePwd "Pwd-Tizi-2" -issuer "C=CN, O=OpenHarmony-Tizi-subCA, OU=OpenHarmony-Tizi-subCA Community, CN=OpenHarmony Application CA" -issuerKeyAlias "OpenHarmony-Tizi-profileCA" -issuerKeyPwd "Pwd-Tizi-5" -validity "365"
8. 将OpenHarmony-Tizi-app-cert.pem中第一部分的密钥,把回车转换为\n字符,放入UnsgnedReleasedProfileTemplate.json的distribution-certificate中。例如:
转换前:
-----BEGIN CERTIFICATE-----
MIICazCCAhGgAwIBAgIFAPERF2IwCgYIKoZIzj0EAwIwgYIxCzAJBgNVBAYTAkNO
MR8wHQYDVQQKDBZPcGVuSGFybW9ueS1UaXppLXN1YkNBMSkwJwYDVQQLDCBPcGVu
SGFybW9ueS1UaXppLXN1YkNBIENvbW11bml0eTEnMCUGA1UEAwweT3Blbkhhcm1v
bnkgQXBwbGljYXRpb24gU3ViIENBMB4XDTIzMDUyMTE0MDU0M1oXDTI0MDUyMDE0
MDU0M1owgYkxCzAJBgNVBAYTAkNOMSIwIAYDVQQKDBlPcGVuSGFybW9ueS1UaXpp
LWFwcC1jZXJ0MSwwKgYDVQQLDCNPcGVuSGFybW9ueS1UaXppLWFwcC1jZXJ0IENv
bW11bml0eTEoMCYGA1UEAwwfT3Blbkhhcm1vbnkgQXBwbGljYXRpb24gUmVsZWFz
ZTBZMBMGByqGSM49AgEGCCqGSM49AwEHA0IABN0OL1RqzWXQWCXpT0tt54aFR0Ul
7pqZYBJaCKT049xUYcfwCHLd0q0IzktNo9nqKIjE5BxOk76w7kHhxwowI2qjazBp
MB0GA1UdDgQWBBQAW6LlxgLrPko7kHS/jbcsqnh4WTAJBgNVHRMEAjAAMA4GA1Ud
DwEB/wQEAwIHgDATBgNVHSUEDDAKBggrBgEFBQcDAzAYBgwrBgEEAY9bAoJ4AQME
CDAGAgEBCgEAMAoGCCqGSM49BAMCA0gAMEUCIQDHIWx4AELONvCoKaQnHQAW0bay
gjR168gmlnGfnFGowAIgfMV5/nIvmRAbpapqO3a2pBKeHFfeU5zel/T1Bgty198=
-----END CERTIFICATE-----
转换后:
-----BEGIN CERTIFICATE-----\nMIICazCCAhGgAwIBAgIFAPERF2IwCgYIKoZIzj0EAwIwgYIxCzAJBgNVBAYTAkNO\nMR8wHQYDVQQKDBZPcGVuSGFybW9ueS1UaXppLXN1YkNBMSkwJwYDVQQLDCBPcGVu\nSGFybW9ueS1UaXppLXN1YkNBIENvbW11bml0eTEnMCUGA1UEAwweT3Blbkhhcm1v\nbnkgQXBwbGljYXRpb24gU3ViIENBMB4XDTIzMDUyMTE0MDU0M1oXDTI0MDUyMDE0\nMDU0M1owgYkxCzAJBgNVBAYTAkNOMSIwIAYDVQQKDBlPcGVuSGFybW9ueS1UaXpp\nLWFwcC1jZXJ0MSwwKgYDVQQLDCNPcGVuSGFybW9ueS1UaXppLWFwcC1jZXJ0IENv\nbW11bml0eTEoMCYGA1UEAwwfT3Blbkhhcm1vbnkgQXBwbGljYXRpb24gUmVsZWFz\nZTBZMBMGByqGSM49AgEGCCqGSM49AwEHA0IABN0OL1RqzWXQWCXpT0tt54aFR0Ul\n7pqZYBJaCKT049xUYcfwCHLd0q0IzktNo9nqKIjE5BxOk76w7kHhxwowI2qjazBp\nMB0GA1UdDgQWBBQAW6LlxgLrPko7kHS/jbcsqnh4WTAJBgNVHRMEAjAAMA4GA1Ud\nDwEB/wQEAwIHgDATBgNVHSUEDDAKBggrBgEFBQcDAzAYBgwrBgEEAY9bAoJ4AQME\nCDAGAgEBCgEAMAoGCCqGSM49BAMCA0gAMEUCIQDHIWx4AELONvCoKaQnHQAW0bay\ngjR168gmlnGfnFGowAIgfMV5/nIvmRAbpapqO3a2pBKeHFfeU5zel/T1Bgty198=\n-----END CERTIFICATE-----\n
9. ProvisionProfile文件签名
java -jar hap-sign-tool.jar sign-profile -keyAlias "OpenHarmony-Tizi-profileCA" -signAlg "SHA256withECDSA" -mode "localSign" -profileCertFile "OpenHarmony-Tizi-profile-cert-release.pem" -inFile "UnsgnedReleasedProfileTemplate.json" -keystoreFile "OpenHarmony-Tizi.p12" -outFile "com.openharmony.signtest.p7b" -keyPwd "Pwd-Tizi-5" -keystorePwd "Pwd-Tizi-2"
10. hap应用包签名
java -jar hap-sign-tool.jar sign-app -keyAlias "OpenHarmony-Tizi-subCA" -signAlg "SHA256withECDSA" -mode "localSign" -appCertFile "OpenHarmony-Tizi-app-cert.pem" -profileFile "com.openharmony.signtest.p7b" -inFile "entry-default-unsigned.hap" -keystoreFile "OpenHarmony-Tizi.p12" -outFile "entry-default-signed.hap" -keyPwd "Pwd-Tizi-4" -keystorePwd "Pwd-Tizi-2"
1. 系统中证书配置文件位于/etc/security/中
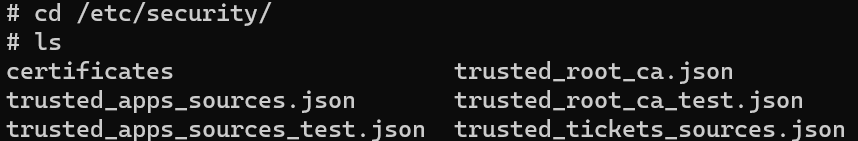
2. 配置 trusted_apps_sources.json 文件。注意“,”符号后面需要加入空格才可正常匹配。
{
"name":"OpenHarmony-Tizi apps",
"app-signing-cert":"C=CN, O=OpenHarmony-Tizi-app-cert, OU=OpenHarmony-Tizi-app-cert Community, CN=OpenHarmony Application Release",
"profile-signing-certificate":"C=CN, O=OpenHarmony-Tizi-profile-cert, OU=OpenHarmony-Tizi-profile-cert Community, CN=OpenHarmony Application Profile Release",
"profile-debug-signing-certificate":"C=CN, O=OpenHarmony-Tizi-profile-cert, OU=OpenHarmony-Tizi-profile-cert Community, CN=OpenHarmony Application Profile Debug",
"issuer-ca":"C=CN, O=OpenHarmony-Tizi-subCA, OU=OpenHarmony-Tizi-subCA Community, CN=OpenHarmony Application CA",
"max-certs-path":3,
"critialcal-cert-extension":["keyusage"]
}
3. 配置 trusted_root_ca.json 文件,将 OpenHarmony-Tizi-rootCA.cer 密钥信息处理后加入到文件中。
"C=CN, O=OpenHarmony-Tizi-rootCA, OU=OpenHarmony-Tizi-rootCA Community, CN=OpenHarmony Application Root CA":"-----BEGIN CERTIFICATE-----\nMIICQzCCAemgAwIBAgIEUwKY8TAKBggqhkjOPQQDAjCBhTELMAkGA1UEBhMCQ04x\nIDAeBgNVBAoMF09wZW5IYXJtb255LVRpemktcm9vdENBMSowKAYDVQQLDCFPcGVu\nSGFybW9ueS1UaXppLXJvb3RDQSBDb21tdW5pdHkxKDAmBgNVBAMMH09wZW5IYXJt\nb255IEFwcGxpY2F0aW9uIFJvb3QgQ0EwHhcNMjMwNTIxMTQwNTI2WhcNMjQwNTIw\nMTQwNTI2WjCBhTELMAkGA1UEBhMCQ04xIDAeBgNVBAoMF09wZW5IYXJtb255LVRp\nemktcm9vdENBMSowKAYDVQQLDCFPcGVuSGFybW9ueS1UaXppLXJvb3RDQSBDb21t\ndW5pdHkxKDAmBgNVBAMMH09wZW5IYXJtb255IEFwcGxpY2F0aW9uIFJvb3QgQ0Ew\nWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAARoC3C5WijOQkLq/AjmtEWkZ+Ooso1p\nRl34qPpEPH0b6iun5wpAlDe20bcCvsiFda2RNXFsqHIl+cj59bnLh83Ro0UwQzAd\nBgNVHQ4EFgQUAIpcSDCk3q3hZ+qwobekzT9vLHAwEgYDVR0TAQH/BAgwBgEB/wIB\nADAOBgNVHQ8BAf8EBAMCAQYwCgYIKoZIzj0EAwIDSAAwRQIhANKbxPqFT5PwURVf\n1Oxa8cf1udcgO0ntULei/GhaQIobAiBH787oVyJtKxMuPw9K6zzhJjBNjZzW0DrK\n/NOyuKLetw==\n-----END CERTIFICATE-----\n"
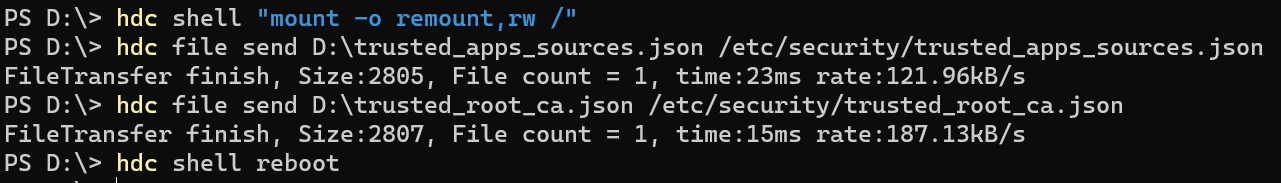
4. 将文件推送回系统中并重启。
hdc shell "mount -o remount,rw /"
hdc file send D:\trusted_apps_sources.json /etc/security/trusted_apps_sources.json
hdc file send D:\trusted_root_ca.json /etc/security/trusted_root_ca.json
hdc shell reboot
5. 安装签名应用。
OpenHarmony Gitee Docs - Hap包签名工具概述
OpenHarmony Gitee Docs - Hap包签名工具指导
OpenHarmony Gitee Docs - HarmonyAppProvision配置文件说明