574
社区成员
 发帖
发帖 与我相关
与我相关 我的任务
我的任务 分享
分享本文基于隐雨隐私计算实训营的课程,【隐私计算实训营 第4期】理论基础:匿踪查询PIR 第2讲_哔哩哔哩_bilibili
目录
1、简单的、基于PHE的实现方式(easy but heavy)
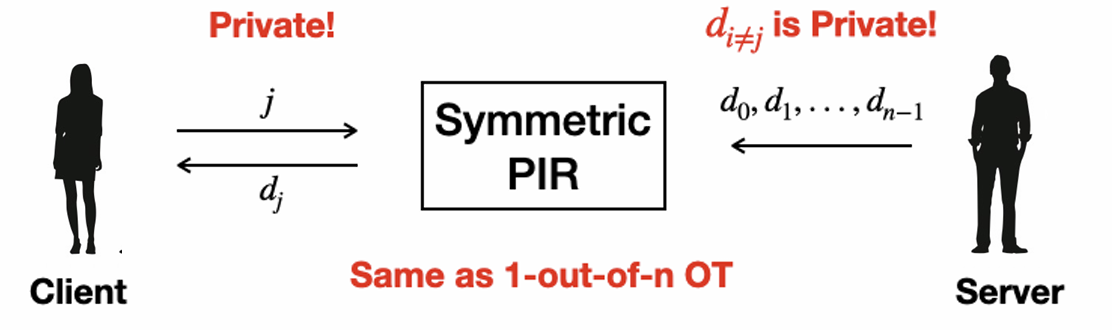
server拥有数据集,而client进行查询,要求client能得到他查询的数据,但是server不知道是什么数据。

还有一种,对称PIR,增加了对server的保护,client只能得到他查询的数据,别的什么也不知道。
(1)单个server PIR(heavy like FHE)
(2)两个server PIR(efficient like DPF)
(1)根据index取值
(2)根据key取值
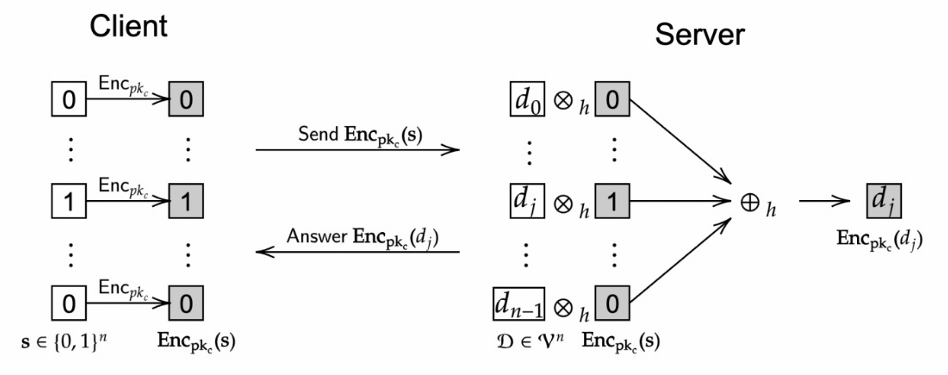
将index编码,只有client需要的index为1,其他都为0,一同加密传输给server
server根据收到的密文对数据进行“与”,最后全部相加,结果发送给client
当存在PHE时,client对其进行解密就能得到所需数据

将多个数据打包到一个同态加密明文
查询向量被压缩成单个密文,在服务器端expand
支持多维度的查询
利用cuckoo hash支持多个查询
query done in seconds from DB with million+ data
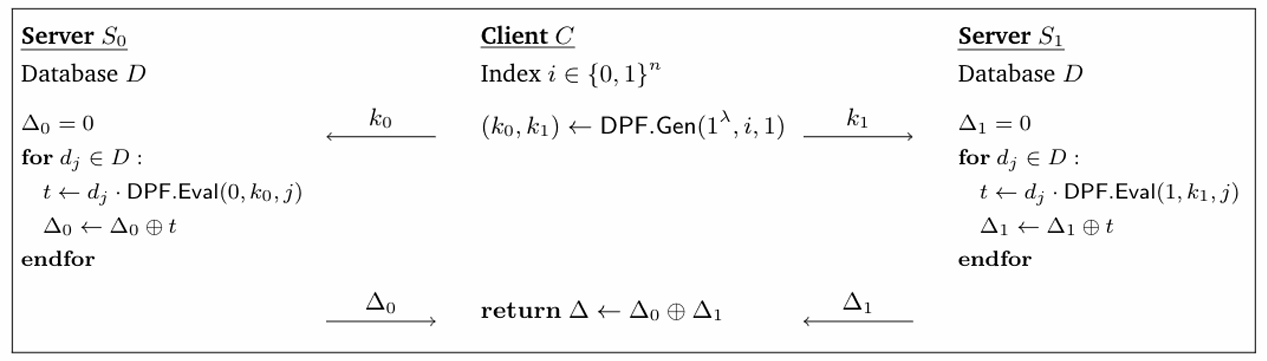
DPF是分布式点函数,很适合于秘密共享

[1] B. Chor, O. Goldreich, E. Kushilevitz, and M. Sudan. Private information retrieval. FOCS 1995.
[2] B. Chor and N. Gilboa. Computationally private information retrieval. In Proc. of 29th ACM Symposium on Theory of Computing, pages 304–313, 1997.
[3] Eyal Kushilevitz and Rafail Ostrovsky. Replication is not needed: Single database, computationally-private information retrieval. In FOCS, pages 364–373, 1997.
[4]Cachin, C., Micali, S., Stadler, M. Computationally private information retrieval with polylogarithmic communication. In: Stern, J. (ed.) EUROCRYPT 1999. LNCS, vol. 1592, pp. 402–414. Springer, Heidelberg (1999)
[5] X. Yi, M. G. Kaosar, R. Paulet, and E. Bertino, Single-database private information retrieval from fully homomorphic encryption, IEEE Trans. Knowl. Data Eng., vol. 25, no. 5, pp. 1125–1134, May 2013.
[6] C. A. Melchor, J. Barrier, L. Fousse, and M. Killijian. XPIR : Private information retrieval for everyone. PoPETs, 2016(2):155–174, 2016.
[7] Sebastian Angel, Hao Chen, Kim Laine, and Srinath Setty. 2018. PIR with Compressed Queries and Amortized Query Processing. In Proc. of S&P. IEEE, 962–979.
[8] Asra Ali, Tancrède Lepoint, Sarvar Patel, Mariana Raykova, Phillipp Schoppmann, Karn Seth, and Kevin Yeo. 2019. Communication-Computation Trade-offs in PIR. IACR Cryptol. ePrint Arch. 2019 (2019), 1483.
[9] H. Corrigan-Gibbs, D. Kogan, Private Information Retrieval with Sublinear Online Time, in: Proc. 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, EUROCRYPT, Zagreb, Croatia, 2020, pp. 1–69.
[10] Benny Chor, Niv Gilboa, and Moni Naor. Private information retrieval by keywords. Technical Report TR-CS0917, Dept. of Computer Science, Technion, 1997.
[11] E. Boyle, N. Gilboa, and Y. Ishai. “Function Secret Sharing: Improvements and Extensions”. In: CCS ’16.
隐语(SecretFlow) https://github.com/secretflow/secretflow